How to Install NMAP using apt
apt update
apt install nmap
How To Use NMAP to scan IPs
| Command | Description |
|---|---|
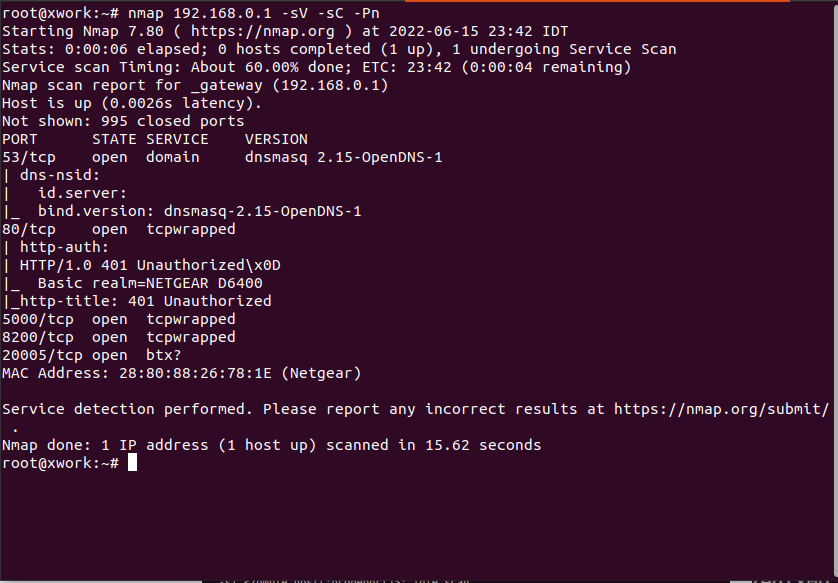
| nmap 10.129.42.253 | Run nmap on an IP |
| nmap -sV -sC -p- 10.122.15.253 | Run nmap Service Enumeration and script scan on an IP |
| nc -nv 192.168.11 5754 | Nmap -sV check banners of the scanned ports and prints them out. If it cannot identify versions try to use nc |
| nmap –script smb-os-discovery.nse -p445 10.10.10.10 | Defined nmap script on an IP |
nmap 192.168.0.45 --script <category> for example brute,malware. | Specific Scripts Category |
nmap 192.168.0.45 -p 80 -A | aggressive option (-A) scans with multiple options sC. sV, O, traceroute |
| more here | ttl time for os detection –packet-trace |
| nmap 10.3.2.55 -p- -sV -sA | TCP ACK scan (-sA) method is much harder to filter for firewalls and IDS/IPS systems |
nmap 10.4.5.6 -sU -Pn -n --disable-arp-ping --packet-trace -p 137 --reason | Discovering Open UDP Ports |
nmap 10.10.5.15 -p- -oA target | specify the option (-oA) to save the results in all formats |
xsltproc target.xml -o target.html | create HTML reports that are easy to read |
NMAP Script Categories
| Category | Description |
|---|---|
auth | Determination of authentication credentials. |
broadcast | Scripts, which are used for host discovery by broadcasting and the discovered hosts, can be automatically added to the remaining scans. |
brute | Executes scripts that try to log in to the respective service by brute-forcing with credentials. |
default | Default scripts executed by using the -sC option. |
discovery | Evaluation of accessible services. |
dos | These scripts are used to check services for denial of service vulnerabilities and are used less as it harms the services. |
exploit | This category of scripts tries to exploit known vulnerabilities for the scanned port. |
external | Scripts that use external services for further processing. |
fuzzer | This uses scripts to identify vulnerabilities and unexpected packet handling by sending different fields, which can take much time. |
intrusive | Intrusive scripts that could negatively affect the target system. |
malware | Checks if some malware infects the target system. |
safe | Defensive scripts that do not perform intrusive and destructive access. |
version | Extension for service detection. |
vuln | Identification of specific vulnerabilities. |
Screenshots gallery